In the article “ENCRYPT Blog Series #4: Privacy Risk Assessment”, various methodologies were presented to carry out a privacy-related risk assessment. Specifically, the ENISA methodology was described, which is related to GDPR and provides support to data controllers and data processors to be GDPR compliant.
In this post, we will look at the possibility of using the ENISA methodology to build a tool that can provide support for conducting a privacy-related risk assessment. Another point on which we will focus will be the application domain, specifically we will see the differences between a general purpose approach and one related to a specific domain.
Using ENISA, a privacy risk assessment tool can be created, to help a user understand the risks and impacts to which their assets may be exposed. It would thus be useful for them to use a framework that helps them identify privacy threats such as LINDDUN. In addition to identifying and assessing privacy threats, the user will also need to identify what types of attacks they may be subject to using the MITRE ATT&CK framework. So, by starting with the ENISA methodology and extending it with the LINDDUN and MITRE ATT&CK frameworks, it is possible to create a new methodology from which to build a privacy risk assessment tool.


In making an assessment that does not take into account the application domain, the user will have to describe all the assets involved in their personal data processing. This methodology has a problem, as the user (in some cases) may underestimate or not consider various threats or vulnerabilities. This may cause an assessment to be completed with gaps, which could result in the user not being guided correctly. If the user were to make an assessment for a specific domain, the system can provide a taxonomy of assets in that domain and can guide the user by pointing out the threats and vulnerabilities to which the assets they have chosen may be subject to. Therefore, the ENCRYPT privacy risk assessment tool will be developed for three application domains – which are healthcare, fintech and CTI.
In order to create a taxonomy for each application domain, it is necessary to compare with domain experts, so that the most common assets can be indicated. Once the assets are listed, for each of them an attack scenario will need to be created, and this will allow us to identify the attack techniques to which it may be vulnerable and privacy threats to which it may be subject. In implementing the taxonomy within the tool, it is necessary to anticipate that it can be expanded with new assets and that we can modify the privacy threats and vulnerabilities assigned to the assets.
Using the methodology described above and once the taxonomies for the various application domains were defined, the privacy risk assessment tool was created. The process the user goes through to complete the assessment is summarized in the figure below.
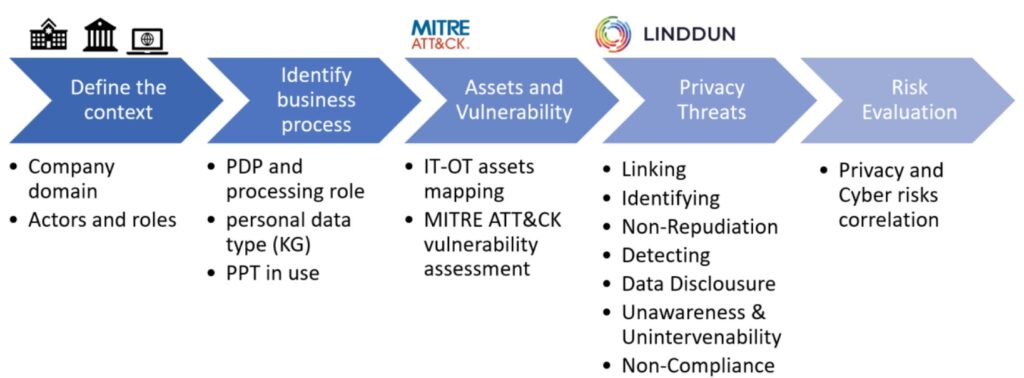
Once the assessment has been completed, the user will be able to see the assessment of the risks to which their personal data processing is exposed, and based on the assessment made, the user can decide what countermeasures to apply to make their assets more secure. The data entered into the privacy risk assessment tool can also be shared with other applications in the ENCRYPT infrastructure.
The methodology that has been developed has enabled us to create this tool, which for now works on only three domains. In the future we could consider expanding the application domains, thus providing support for the compilation of assessments in multiple domains.
